Each year millions of Americans are the victims of fraud or identity theft. In 1997 the Consumer Sentinel Network (CSN) was established to create a secure online database to track complaints filed with the FTC, state law enforcement agencies, and Federal agencies like the IRS and Consumer Financial Protection Bureau.
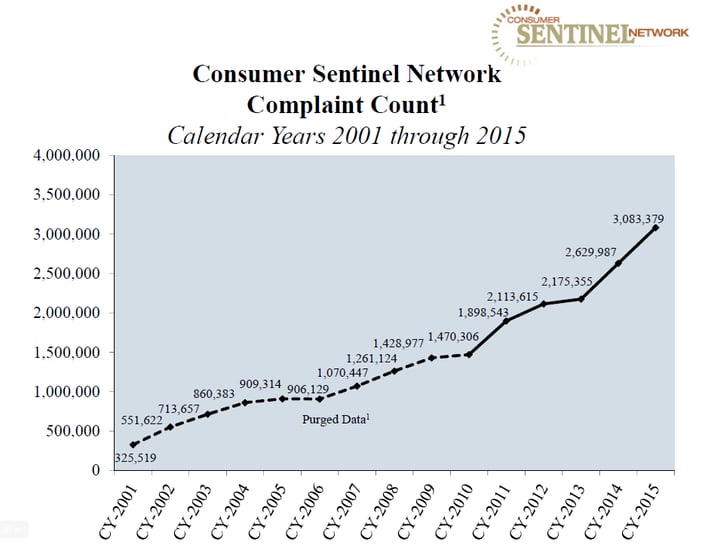
In 2015, the last reported year, CSN received more than 3 million consumer complaints nearly ten times the number reported in 2001. Consumers reported paying a staggering $765M dollars in 2015 for fraud complaints.
Debt Collection was the number one complaint category with 29% of the overall complaints followed by Identity Theft with 16%. For a complete listing go to the FTC.gov website.
Identity theft and identity fraud are often mistaken interchangeably, but they are different. Identity theft occurs when a thief gets access to your social security number, credit card number, driver’s license number or another piece of personal information for the purposes of impersonating you. Once a thief has your information they open a new credit card account, cell phone account, or other account in your name – this is known as “true name identity theft”. If the thief decides to access your existing accounts, it is referred to as “account takeover.”
Identity fraud is a crime in which a thief creates a fictitious person using various other sources of personal story, rather than stealing someone’s identity. However, a person committing identity fraud typically commits “true accounts identity theft” as well by opening up lines of credit in the fictitious person’s name.
When it comes to identity theft the victim is the individual whose identity was stolen as well as the merchants, utilities or other businesses defrauded by the thief. Victims of identity fraud are the credit card companies, merchants, lenders or other businesses, but not the fictitious person. According to CSN this is how identity theft victim’s information was misused in 2015:
- Government Document & Benefits Fraud – 49.2%
- Credit Card Fraud – 15.8%
- Phone or Utilities Fraud – 9.9%
- Bank or Loan Fraud – 9.4%
- Employment-related Fraud – 3.3%
- Other Identity Theft – 19.2%
*14% of complaints include more than one type of identity theft
While we all think of high profile “hacks” involving theft of large customer databases from retail establishments or banks – other businesses aren’t immune. Firewalls didn’t stop thieves from hacking Target, Home Depot, or TJ Maxx. Physical access controls didn’t stop Private Manning from releasing hundreds of thousands of military secrets to WikiLeaks. Background checks didn’t stop Edward Snowden.
Simply keeping information under lock and key – inaccessible to the public is not a foolproof measure to prevent Identity theft and privacy breaches. One sobering statistic from Gartner is 85% of privacy breaches go undetected.
For more than a decade Extract Systems has been helping organizations redact personally identifying information from their documents. Our technology, ID Shield, has been used to identify 35 different types of sensitive information, and process in excess of 3 billion image pages in a variety of industries to include government, healthcare, colleges and universities, law firms, and more.
If you are considering making document available online, trying to obtain PCI compliance, protect against the unintended Release of Information to meet HIPAA requirements, or just want to better protect your records – redaction should be part of your strategy. To learn more about ID Shield or to schedule a demo please contact me at troy_burke@extactsystems.com or call (608) 821-6534.